Dark Web Monitoring is a premium feature for securing your Google Workspace tenant and other properties from compromised credentials that have been detected on the dark web. Dark Web Monitoring alerts Google Workspace administrators when their employee's emails and passwords have been compromised, enabling them to take proactive steps to secure accounts at risk. They can then leverage Google Workspace’s powerful audit reporting and Spanning search capabilities to determine if malicious activity has taken place and restore any corrupted data in just a few clicks.
See these topics for details:
Dark Web Monitoring matches the account detected to the account in Google Workspace Directory and Spanning Backup for Google Workspace. The resulting matrix is Google Workspace: Active, Suspended, and Deleted; and Spanning: Protected and Not Protected.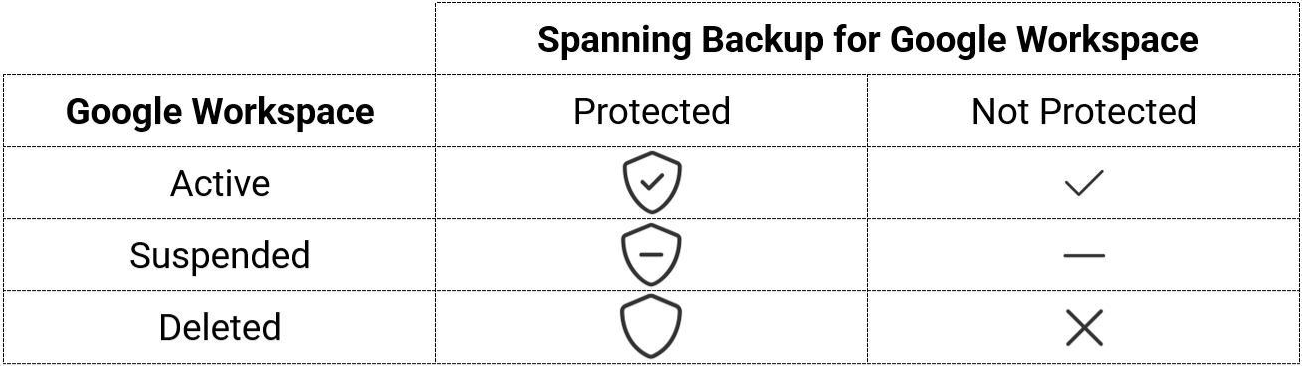
A description of each status is given here:
- Spanning Protected – There is a Spanning Backup for Google Workspace license associated with this account.
- Spanning Not Protected – The account is not licensed for Spanning Backup for Google Workspace.
- Google Workspace Active – The account was found in Google Workspace and is not disabled.
- Google Workspace Suspended – The account was found in Google Workspace and is suspended.
- Google Workspace Deleted – The account was not found in Google Workspace. Note, this may include email aliases.
At Spanning, we are happy to deliver one of the most requested features for our Dark Web Monitoring capability since the service was announced. Spanning Administrators can now resolve compromised records so that the records are removed from the list of compromises.
To review and resolve compromised records
NOTE Once you confirm the action to mark compromised records resolved, they no longer display in Spanning Dark Web Monitoring. The records cannot be retrieved. This action is logged in the Audit Log (see Viewing application activity).
- Get started by navigating to the Dark Web tab.
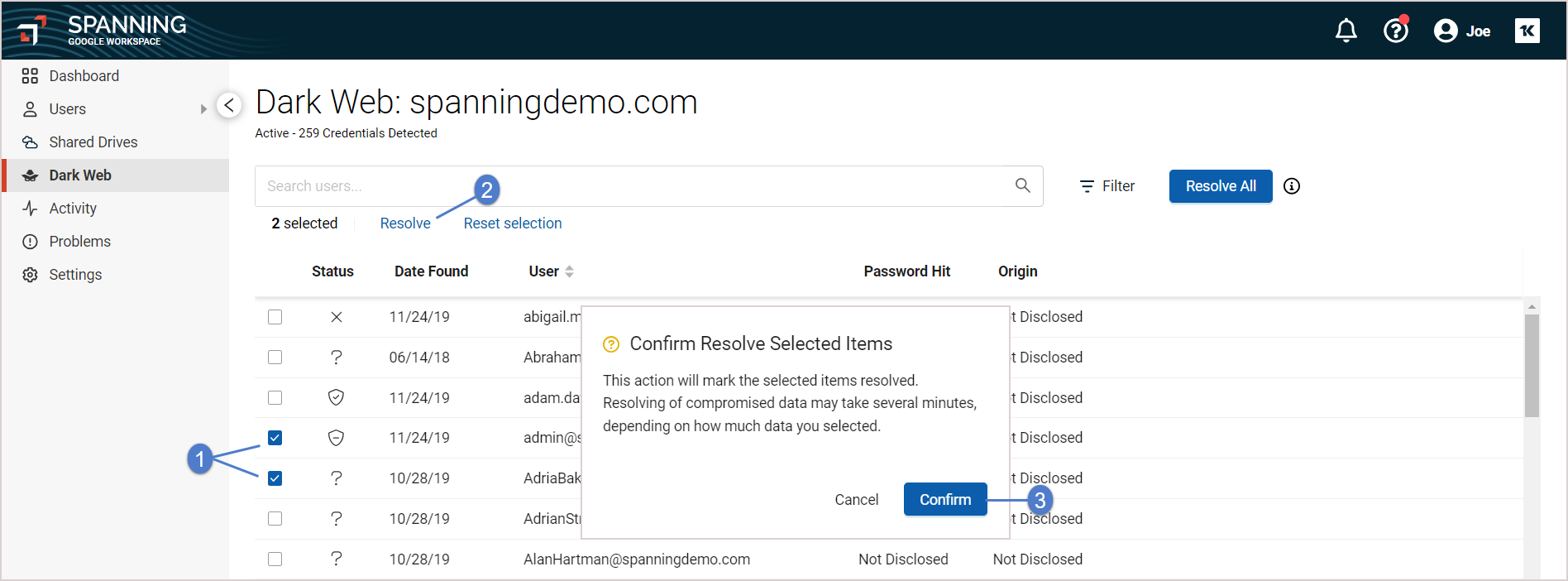
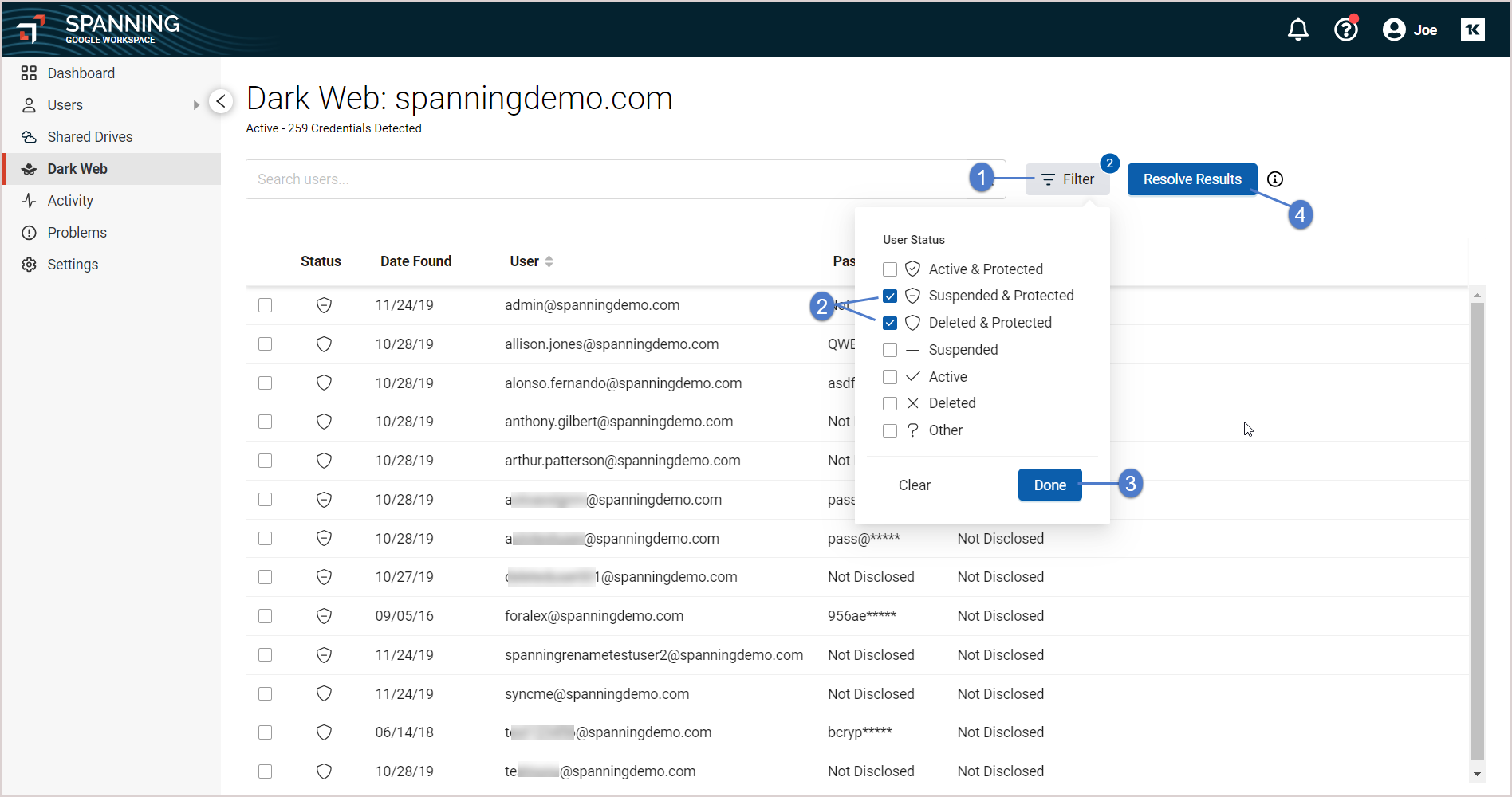
- With the compromise list in view you can select, search, or filter the records in the compromise list.
- Once you have either selected or filtered the list you have these resolution options:
- Selected – Resolves only the selected items in the compromised list.
- Resolve All – Resolves all items in the compromised list.
- Resolve Results (Filtered) – Resolves all compromised items in the current view. If the view is filtered, only the filtered items are resolved. If the view is not filtered, all items are resolved, clearing the list.
If you choose a large list of records to be resolved they are processed in batches of 500. The process may take a few moments to complete.
When Spanning Backup for Google Workspace receives breach data for a domain, it may include the entire plain text password or a password hash. Spanning truncates the password to 10 characters and masks the last 5 before we store it in our database or show it to an administrator. We feel that the IT Admin doesn't need the whole password to have the conversation with the person who is breached. They can say, "Do you still use a password that starts with passw*****?", and still have a meaningful conversation about the significance of strong passwords and password security.
Spanning Backup for Google Workspace Dark Web Monitoring is domain-level protection. Domains in the tenant are evaluated for compromised credentials and the result of the monitoring can result in accounts that are associated with your domain but may not be an active account in Google Workspace Directory. For example, the Acme Corp Marketing department maintains a social media presence using marketing@acmecorp.com. This marketing address is not associated with a Google Workspace Directory account, it is just an email alias. This email address and the password mypass@word are used to secure Canva, Twitter, Facebook, and Instagram. If these credentials are part of the Instagram or Canva breaches, they would appear in the Dark Web Monitoring report as marketing@acmecorp.com and mypas*****. Even though there is no user account in Google Workspace AD, this breached account represents a risk to the Acme Corp social media presence if the password is reused.